 PHOTO: the ineffable King George and all its magic. Courtesy Chiara Rosso.
PHOTO: the ineffable King George and all its magic. Courtesy Chiara Rosso. "NoTanDistintos" 209
Driving Program: Alberto "Tano"
Rosso and Blanco Guillermo Alvarado
technical operation: Alexis Naus
Date: Saturday November 27, 2010
hours: 18:00 to 21:00
radio: FM FLORES 90.7
internet: http://www.radiofmflores.net/
LISTENING
BLOCK 1: Introduction and Blues - LISTEN
BLOCK 2: Interview and Blues - LISTEN
BLOCK 3: Live Music - LISTEN
BLOCK 4: Interview and Blues -
LISTEN BLOCK 5: Agenda and Jazz - LISTEN
BLOCK 6: Interview and Blues - LISTEN
BLOCK 7: Farewell and Blues - LISTEN
MUSICAL PROGRAMMING
Jimmi Hendrix "Wipe the Sweat"
DISC: Two Great Experiences (1965)
MUSICIANS: Jimi Hendrix (guitar) Lenny
Youngblood (tenor sax) John Winfield (organ)
Hank Anderson (bass) Jimmy May (drums)
David M'ore "Shame Shame Shame (author Kenny Wayne Shephard)
DISCO: From the Other Side of the River (2009)
MUSICIANS: David M'ore (vocals, guitar)
Kirk Bowman (bass) Wade Olson (drums)
David M'ore "Foxy Lady" (author Jimmi Hendrix)
DISCO: From the Other Side of the River (2009)
MUSICIANS: David M'ore (vocals, guitar)
Edgard San Gabriel (bass) Wade Olson (drums)
David M'ore "Sweet Little Angel" (author BB King)
In Vivo Studies in FM FLORES 90.7 (27 / 11 / 2010 )
MUSICIANS: David M'ore (vocals, guitar)
David M'ore "You Are Not So Good"
DISCO: From the Other Side of the River (2009)
MUSICIANS: David M 'ore (vocals, guitar)
Kirk Bowman (bass) Wade Olson (drums)
David M'ore "The Sun Is Shining"
DISCO: From the Other Side of the River (2009)
MUSICIANS: David M'ore (vocals, guitar)
Alex Diaz (bass) Wade Olson (drums)
Federico Bozas "Little Wing" (author Jimmi Hendrix)
Live in Thailand (2005)
MUSICIANS: Federico Bozas (vocals, guitar)
Javier Viñas (guitar), Silvio R. Marzolini (piano)
Rodrigo Barrientos (alto saxophone) Jorge Oss (bass) Bozas Willy (drums)
Marcus Bonfanti "Will Not Play Your Game"
DISCO: What Good Am I to You (2010)
MUSICIANS: Marcus Bonfanti (vocals, guitar)
Elizabeth Brown (vocals), Paddy Milner (keyboards) Scott
Wiber (bass) Alex Reeves (drums)
Robert Cray "Anytime"
DISCO: Cookin 'in Mobile (2010)
MUSICIANS: Robert Cray (vocals, guitar)
Jim Pugh (keyboards) Richard Cousins \u200b\u200b(bass) Tony Braunagel
(drums)
Hoochie Coochie Girls "It Hurts me Too " (author Tampa Red).
Recorded Live on the Radio (20 / 11 / 2010)
MUSICIANS: Jessica County (vocals, bass) Pamela Smith (guitar)
Ximena Monzón (harmonica)
Grant Green Jr & Reuben Wilson "Sweet Home Chicago" (author Robert Johnson)
ALBUM: The Godfathers Of Groove (2007)
MUSICIANS: Grant Green Jr. (guitar), Reuben Wilson (organ)
Jerry Jemmott (bass) Bernard Purdie (drums)
King George "Blues Gonna Get You"
DISCO: Afrobeat (2000 )
MUSICIANS: King George (vocals, guitar) Jim
Addler (guitar) Back Brothers (sax, piano)
Neucler Caroline (bass) Abdul Ali (drums) Johan Eboule (percussion)
King George " Help me "
DISCO: Afrobeat (2000)
MUSICIANS: King George (vocals, guitar) Jim
Addler (guitar) Back Brothers (sax, piano) Caroline
Neucler (bass) Abdul Ali (drums) Johan Eboule (percussion)
King George medley
In Vivo Studies in FM FLORES 90.7 (27 / 11 / 2010)
MUSICIANS: King George (vocals, guitar)


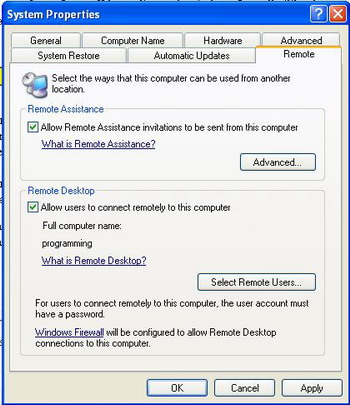
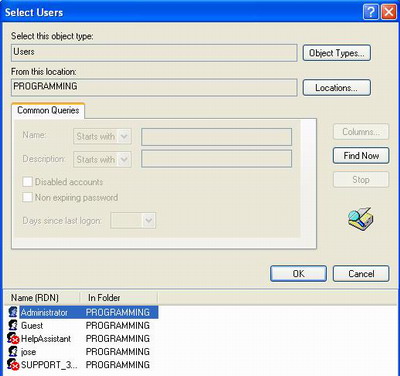
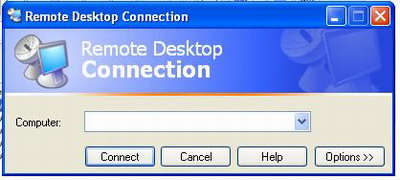

 This command displays the folders and files located on drive f.
This command displays the folders and files located on drive f. 


 FORMAT external command. To format a floppy / hard disk
FORMAT external command. To format a floppy / hard disk 

 DIR / ad
DIR / ad 
 Example usage:
Example usage: 
 Enabling the hidden attribute as well as attributes of the system in the README.TXT file
Enabling the hidden attribute as well as attributes of the system in the README.TXT file  attrib + h + s README.TXT
attrib + h + s README.TXT 

 [Version Serial number].
[Version Serial number]. 
 License VLK Official
License VLK Official 
 http://en.wikipedia.org/wiki/Vlk
http://en.wikipedia.org/wiki/Vlk  CRACKING (SN
CRACKING (SN  these?
these?  So ... please your own responsibility ...
So ... please your own responsibility ...  Pertamax:
Pertamax: 
 Once in check with
Once in check with  LEGITCHECK.HTA Tool
LEGITCHECK.HTA Tool 